ClickFix And FileFix: Deconstructing The Evolving Threat Of Clipboard Hijacking Attacks
The modern threat landscape is increasingly defined by attacks that bypass technical security measures by exploiting the weakest link: the human user. ClickFix and its recent evolution, FileFix, represent a potent and rapidly growing wave of social engineering attacks that leverage common user habits to facilitate self-infection.
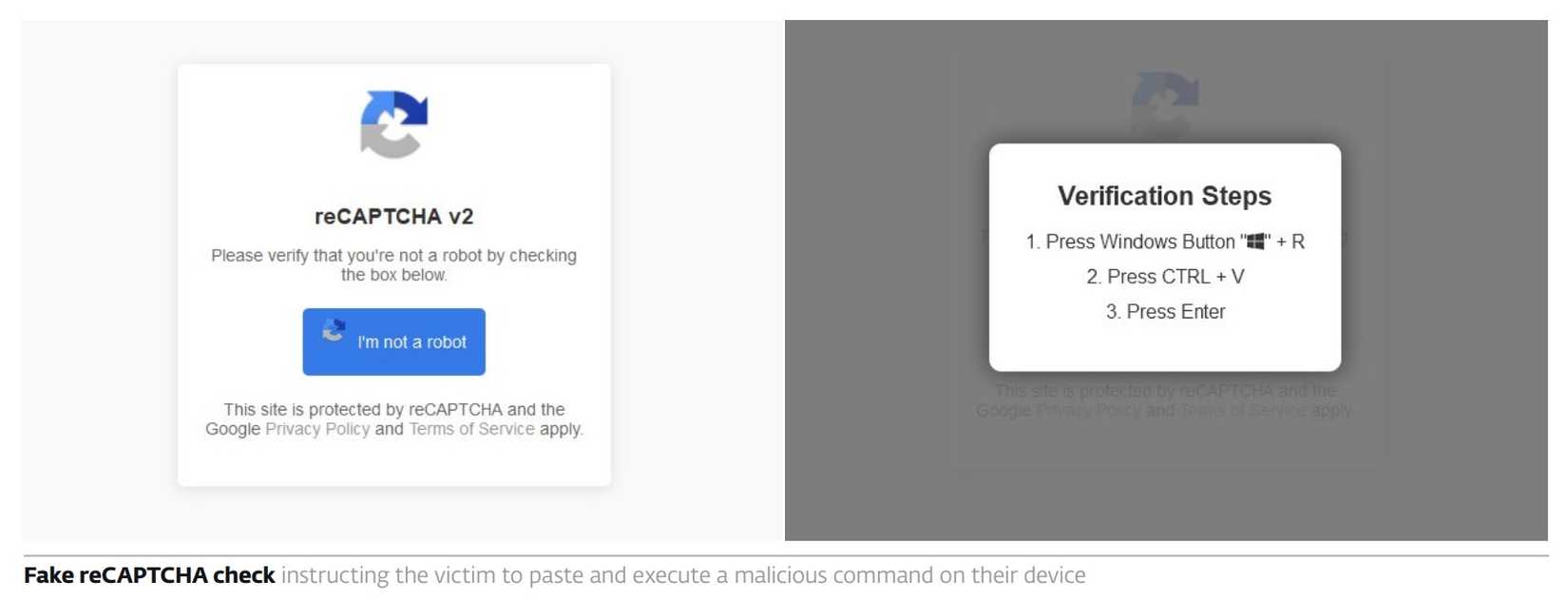
These sophisticated campaigns trick users into executing malicious code that has been silently loaded into their system's clipboard by a deceptive webpage posing as a CAPTCHA verification, software update, or critical system repair dialog.
The Core Mechanics Of ClickFix Social Engineering
Bypassing Protections Through User Trust
ClickFix is not a type of malware itself, but rather an ingeniously simple delivery mechanism that sidesteps typical browser and operating system security warnings. The primary goal is to convince the victim to execute a payload command voluntarily.
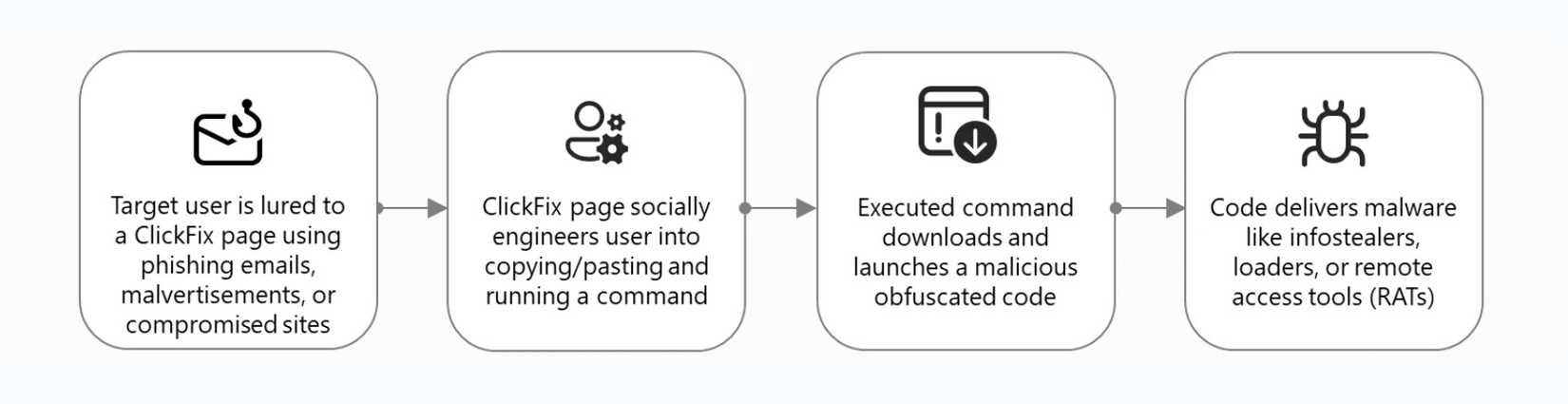
The process generally unfolds in three critical stages:
- Deception: The victim navigates to a malicious, yet highly polished, webpage (often via phishing or malvertising) claiming a fatal error or verification failure.
- Clipboard Hijacking: Using simple JavaScript, the webpage silently copies a short but harmful command (usually a PowerShell or shell script) into the user's clipboard. This action is invisible and requires no interaction from the user.
- Voluntary Execution: The page instructs the victim to open a system application—such as the Run dialog, PowerShell, or Terminal—and paste the "fix code" and hit Enter. The command, once executed, downloads and runs the actual second-stage malware (e.g., an infostealer, ransomware, or RAT).
Because the victim is the one initiating the execution process, the action is often trusted by the operating system's built-in defenses, making it alarmingly effective. This is why threat reports, such as those from Microsoft and ESET, have noted massive spikes in ClickFix activity since its emergence in 2024.
FileFix: The Evolution Targeting File Explorer
Adapting To New Execution Vectors
A variation of the attack, dubbed FileFix by security researchers, demonstrates the adaptability of this social engineering technique. Instead of directing users to the Run dialog or PowerShell, FileFix campaigns instruct the victim to paste the malicious command directly into the address bar of Windows File Explorer and hit Enter.
Since the File Explorer address bar supports running executables and shell commands, this method achieves the same result: immediate execution of the command-line payload, leading to the download of secondary malware. This evolution showcases the attackers' continued experimentation with trusted OS components to achieve their nefarious goals.
Mitigating The Risk: A Defense In Depth Strategy
Technical Controls And User Education
Given the nature of the ClickFix attack—relying on human action rather than a system vulnerability—a successful defense requires a combination of strong technical controls and constant security awareness training.
The following steps are critical to avoiding and recovering from such attacks:
- Zero Trust Principle: Never, under any circumstances, paste and execute commands from an external or unexpected source into your operating system's command prompt (Run, PowerShell, Terminal, File Explorer Address Bar). Legitimate services do not require this action for verification or repair.
- Source Verification: Treat any unexpected "fix" or "verify" prompt with extreme skepticism. If a trusted service (e.g., Cloudflare, Booking.com) seems to be asking for a fix, close the tab and navigate to the service's official website directly.
- Phishing Awareness: Since ClickFix often starts with phishing emails or malicious advertisements, rigorously apply phishing best practices: check email sender addresses, hover over links to verify destinations, and avoid clicking suspicious attachments.
- Endpoint Protection: Ensure that next-generation antivirus (NGAV) and Endpoint Detection and Response (EDR) solutions are running and up-to-date. Modern security tools are better at monitoring and flagging unusual command-line activity (e.g., a short PowerShell command attempting to download an executable from a non-standard source).
- Active Monitoring: Utilize operating system security features like Windows SmartScreen and Defender, which can often block the final payload file even if the initial execution command is successful.
The continued success and rapid spread of ClickFix (demonstrated by ESET's reported 500% increase in activity) confirm that attackers will continue to prioritize social engineering as long as it delivers a high rate of successful compromise. Vigilance remains the most effective defense.
FAQs On Clipboard Attacks And Prevention
How does JavaScript secretly load a command into my clipboard?
Malicious websites utilize the standard browser API for clipboard access, usually through the document.execCommand('copy') method or the newer navigator.clipboard.writeText() API. While modern browsers often require a user-initiated event (like a click) to grant clipboard access, attackers disguise this by linking the malicious copy function to an innocuous action, or by triggering it upon page load or mouse movement, often out of the user's view.
Are Macs and Linux systems vulnerable to ClickFix/FileFix?
Yes, the underlying social engineering principle and the clipboard hijacking mechanism are OS-agnostic. While the specific commands used in ClickFix (e.g., PowerShell) are Windows-specific, attackers can easily substitute them with equivalents for macOS (e.g., shell commands executed via Terminal) or Linux. Security firms have already documented ClickFix campaigns successfully targeting macOS users.
What steps should I take immediately if I accidentally paste and run the malicious command?
If you suspect you have executed a malicious command, you must immediately disconnect your device from the internet (turn off Wi-Fi or unplug the Ethernet cable) to halt any ongoing data exfiltration or communication with the attacker's Command & Control (C2) server. Next, perform a full system scan using a reliable, up-to-date security solution, and change all critical passwords (especially email and bank accounts) from a separate, clean device.


Posting Komentar untuk "ClickFix And FileFix: Deconstructing The Evolving Threat Of Clipboard Hijacking Attacks"